The government’s cavalier approach to security for its rapidly expanding digital governance and identity systems should be enough to give all UK citizens pause — if only they knew about it!
Some time roughly a month ago, hackers broke into the UK’s Legal Aid Agency’s IT system and made off with a “significant amount of personal data” belonging to hundreds of thousands of legal aid applicants dating all the way back to 2010. That data, according to The Register, could include applicants’ contact details, home addresses, dates of birth, criminal histories, employment statuses, and financial data such as contribution amounts, debts, and payments.
While the attack itself was detected on April 23, it wasn’t made public until May 6. It wasn’t until May 16 that investigators realised, or at least publicly acknowledged, that the damage was “more extensive than originally understood and that the group behind it had accessed a large amount of information relating to legal aid applicants.”
The UK’s retail sector has also been hit by a spate of cyberattacks. Last week, the British high street retailer Marks & Spencer finally came clean that the hackers that had brought down their website for a whole month had also made off with reams of personal customer information, fuelling speculation that ransomware was involved.
The stolen data included masked payment card details (usually the last four digits of a payment cards). Given that M&S has 9.7 million active customers — equivalent to almost one out of six UK citizens — the potential impact of the breach could be significant, especially given the sensitivity of some of the data compromised. As is often the case in these kinds of incidents, the hackers are believed to have gained access to M&S’ IT system through third party providers.
The damage to M&S, both financial and reputational, has been significant. Its online platform is still down over four weeks after the initial attack, setting it back over 60 million pounds ($80 million) in lost profit, according to analysts. In the three weeks immediately following the cyberattack, M&S lost around £1 billion of its market value on the London Stock Exchange. In a statement posted to the London Stock Exchange last Tuesday, M&S’ management said:
“Today, we are writing to customers informing them that due to the sophisticated nature of the incident, some of their personal customer data has been taken. Importantly, the data does not include usable payment or card details, which we do not hold on our systems, and it does not include any account passwords. There is no evidence that this data has been shared.
But the retailer has no way of confirming that the data isn’t being shared. These recent data breaches underscore a worrying trend in today’s almost digital-everything society: our personal data is becoming less and less safe in the hands of both government and corporations as more and more of it is brought online. To quote Prof Sandra Wachter, a data ethics expert at the Oxford Internet Institute, “welcome to the Internet,” where “everything is hackable.”
Inauspicious Beginnings
The reason why this should be of particular concern to UK citizens is two-fold.
First, the UK government, like the EU and many national governments, is in the process of rolling out a digital identity wallet, branded Gov.UK, as part of its “One Login” digital governance system. If successful, One Login could end up holding just about every data point imaginable on UK citizens. Which brings us to the second reason: when it comes to protecting citizens’ data and running IT operations in general, the UK government has a horrid track record.
On July 5, the day Keir Starmer became UK prime minister, we wagered that a Starmer government would intensify the push to roll out a digital identity system in the UK — a country that has, until now, resisted all recent attempts to introduce an ID card system, including, most notably, by Starmer’s backroom consultant and mentor, Tony Blair. At the risk of blowing our own trumpet, that is exactly what has happened.
Late last year, the propaganda push for digital identity kicked into gear. After studiously ignoring the issue for years, the legacy media suddenly began trying to manufacture public complacency and consent for the government’s digital identity — and by extension, CBDC — agenda. That agenda, both in the UK and elsewhere, is ultimately about expanding government — and with the CBDCs, central bank — control over the increasingly restive populaces.
Blair’s non-profit, the Tony Blair Institute for Global Change, claims that introducing digital ID will “improve governance, facilitate greater inclusion, fuel economic growth” and “make information more secure”. However, as Michael Orlowski points out in a recent article for Spike, the recent revelations from the One Login juggernaut suggest otherwise:
Digital ID will not ‘improve governance’ or ‘facilitate greater inclusion’. Far from it. What it will do is put our private data at serious risk. This is a threat to us all.
One Login was launched in 2021 by Michael Gove after the Tory government’s previous attempt to launch a digital ID and verification system, called Verify, failed after burning through £400million of public funds. Following a slow start, One Login now has six million users.
The system appears to have been inspired by other digital government service and identity systems already established in Europe, including Estonia’s e-Estonia and Ukraine’s Diia, which was brought down by Russian hackers in December.
As readers may recall, the UK signed a digital trade agreement with Kiev in late 2022 that included a provision for collaborating on digital identity. London, together with its partners in the US and the EU, had helped to fund the Zelensky government’s development and roll out of Diia.
A year later, the UK signed a Memorandum on Cooperation with Ukraine and Estonia setting out their commitment to a “trilateral programme of activity on e-governance and digitalisation”. The text of the memorandum paints a pretty picture of the transformational potential of digital governance:
Digital technologies have the capacity to revolutionise every aspect of how governments function, contributing to increased efficiency in the delivery of public services. Digitalisation can also facilitate transparent processes and accountable decision-making and improve investor confidence.
A Perfect Bonanza
But if the systems are not properly secured, they risk creating a perfect bonanza of lucrative data for hackers and nation-state adversaries — of which, let’s face it, the UK has plenty. They could also create key points of vulnerability within the UK government and civil service’s IT systems.
One Login’s early beginnings hardly inspire confidence. Take, for example, the fact that it has already lost its certification against the government’s own digital identity system trust framework. From Computer Weekly:
The government’s Gov.uk One Login digital identity system has lost its certification against the government’s own trust framework for digital identity systems.
Computer Weekly has learned that a key technology supplier to One Login chose to allow its certification to lapse, and as a result, One Login has also been removed from the official accreditation scheme.
All suppliers of digital identity systems in the UK are expected to comply with the Digital Identity and Attributes Trust Framework (DIATF) if their software is to be used for any public services.
For example, companies that wish to provide identity verification for services such as right to work, right to rent or the Disclosure and Barring Service for vetting individuals, must conform with DIATF. More than 50 online government services already use One Login, and further services are planned that will expand the scope of DIATF registration. Currently, more than 50 products have received certification against the framework.
The Government Digital Service (GDS) achieved DIATF approval for One Login in December 2024, ahead of the announcement by technology secretary Peter Kyle in January that One Login would be used for identity verification for the forthcoming Gov.uk Wallet, which will store digital versions of official documents such as driving licences.
Kyle’s announcement caused shockwaves among existing DIATF suppliers, which saw the government entering the commercial sector and potentially competing with their products.
However, the use of One Login must be called into question while its DIATF certification has lapsed. The system uses technology from supplier iProov as part of the biometric authentication process for users proving their identity. Last month, iProov failed to renew its DIATF compliance, so the One Login registration automatically expired.
Horizon All Over Again?
This is one of a host of problems with One Login that have come to light in recent months. Unfortunately, they have received scant attention in the legacy media, with The Telegraph standing out as a notable exception. In April, it published an article by Orlowski titled “‘It’s Horizon All Over Again’: Return of Digital IDs Sparks Security Concerns“, in reference to the Post Office Horizon scandal that ruined the lives of thousands of Post Office submasters and that was the brainchild of the Tony Blair government.
In his article, Orlowski reveals that One Login’s cyber security failings are already potentially putting citizens’ personal data at risk:
Developers were given top level system access without the required level of security vetting and high numbers of defects were reported, according to an audit from 2023.
In addition, the project’s top management at the Government Digital Service (GDS) were unaware that parts of the system were being developed in Romania, a country known as a cyber crime hotspot.
The Government insists the allegations are historic and security systems have been brought up to standard since then. Officials dismiss any suggestion that the public’s data is unsafe.
However, the allegations of poor cyber security practices during the crucial building phase have raised concerns.
“The Government’s response does not deny that there have been ‘concerns’ in the past and relies on everything being in order now. But what may be embedded in the system?” asks Baroness Neville-Jones, a former Home Office minister.
The security of the system is of vital importance.
One Login is designed to be a critical cog in a much larger machine, unlocking access to other government services – from tax to benefits. It also processes personal information ranging from passports to biometric information. Potential flaws in the system could leave it vulnerable to fraud, or worse.
The government insists that the system will be voluntary, but so too did many other governments that ended up making digital identity legally obligatory, or de facto mandatory, from Estonia to India. As part of the first phase of its mass roll out, the UK government is launching a digital veteran card this year that the RAND Corporation described as “an opportunity to improve access to services” for former military personnel.
As in the US, Digital driving licenses are also coming down the pipe. The government is also launching a new identity verification service for company directors and individuals with corporate control. UK Companies House, which maintains the UK’s company register, says the process is currently voluntary but it is expected to become mandatory after identity verification becomes a legal requirement later this year as required under the Economic Crime and Corporate Transparency Act.
Just like that, voluntary affiliation becomes mandatory participation.
At the same time, serious concerns remain about the security of the UK’s One Login platform, as Bryan Glick, the editor in chief of Computer Weekly, laid out last week in a scathing editorial:
External security tests on the government’s flagship digital identity system, Gov.uk One Login, have found serious vulnerabilities in the live service, Computer Weekly has learned.
A “red teaming” exercise conducted in March by IT security consultancy Cyberis discovered that privileged access to One Login can be compromised without detection by security monitoring tools.
According to Cyberis, red teaming tests the resilience of systems by simulating the tactics, techniques and procedures of cyber attackers to show how well an organisation can detect and respond to an incident.
Computer Weekly has been asked by the Department for Science, Innovation and Technology (DSIT) not to reveal further details of the vulnerability while the Government Digital Service (GDS) seeks to fix the problem.
Compromising the highest levels of access to a system risks exposing personal data and software code to any cyber attackers able to exploit the vulnerability.
A government spokesperson said: “Delivering best practice, we routinely conduct red teaming exercises to test security infrastructure. Where issues are found, we work urgently to resolve them.”
The existence of a serious current vulnerability will raise further concerns over the security of One Login, which is intended to be the way that citizens prove their identity and log in to most online government services.
Keep in mind: this is not a system currently under development but one that was launched four years ago. As Glick notes, One Login already has six million users, and is used to access more than 50 online services. Yet the security flaws persist:
Last month, Computer Weekly revealed that GDS was warned by the Cabinet Office in November 2022 and the National Cyber Security Centre (NCSC) in September 2023, that One Login had “serious data protection failings” and “significant shortcomings” in information security that could increase the risk of data breaches and identity theft.
GDS said the concerns were “outdated” and arose “when the technology was in its infancy in 2023”, despite One Login being used at that time to support live services. “We have worked to address all these concerns as evidenced by multiple external independent assessments. Any suggestion otherwise is unfounded,” said a spokesperson, at the time…
A whistleblower first raised security concerns about One Login within GDS as long ago as July 2022. The issues identified included system administration being performed through non-compliant devices with a risk of transmitting security vulnerabilities, such as malware or phishing attacks, that could compromise the live system.
The NCSC recommends that system administration for key government services should be conducted from a dedicated device used only for that purpose, known as a privileged access workstation (PAW), or alternatively to use only “browse down” devices, where the security level of the device is always the same or greater than the system being managed. The whistleblower warned that a lack of PAWs and use of browse-up administration were significant risks.
Computer Weekly subsequently revealed that the One Login team has yet to fully meet NCSC guidelines – the system only complies with 21 of the 39 outcomes detailed in the NCSC Cyber Assessment Framework (CAF) – an improvement on the five outcomes it successfully followed a year ago….
Speaking to Computer Weekly about the security concerns, [Conservative MP] Clement-Jones said: “How is the government’s flagship digital identity system failing to meet standards so badly, given that it is expected to shortly form an essential part of our immigration controls? We need answers and quickly.”
One Login will not just form an essential part of the UK’s immigration controls. As the Secretary of State for Science, Innovation and Technology Peter Kyle* notes, One Login will underpin the forthcoming Gov.uk Wallet, which will be used to deliver digital versions of key government documents, such as driving licences. And that will be just the beginning. As the now-notorious WEF infographic shows, the ultimate goal of digital identity is that it reaches into every aspect of governance and business, touching every facet of our daily lives:
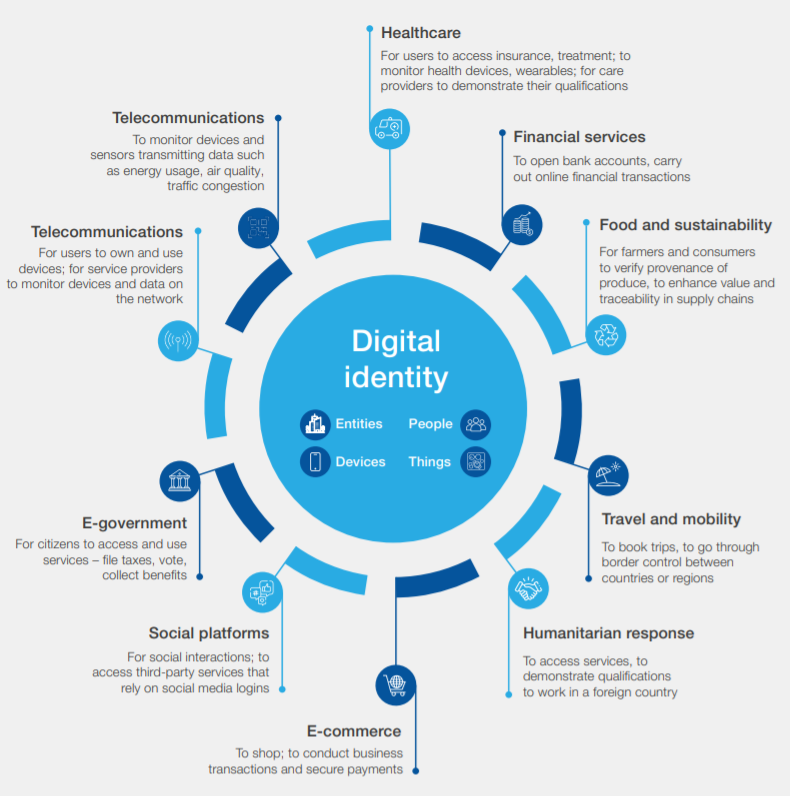
Along the way, platforms like One Login will hoover up vast stores of precious data about our lives, and that data is unlikely to be secure. In a world where pretty much all of our online data is hackable, the British government’s cavalier approach to Internet security, including its outsourcing of work to other countries like Romania, a nation that ranks sixth on the World Cybercrime Index, should be enough to give all UK citizens pause — if only they knew about it!
* Kyle is a former special advisor in the Cabinet Office under Tony Blair’s government, and has close ties to the former prime minister and his non-profit, the Tony Blair Institute for Global Change (TBI). In his role as Secretary of State for Science, Innovation and Technology, Kyle heads up a department with a dizzying range of responsibilities, including overseeing the country’s digital infrastructure, digital public services, AI and space science.
In a recent Guardian article, Kyle was accused of being too close to Big Tech, including TBI’s sugar daddy, Larry Ellison, who recently told investors that AI will usher in a new era of surveillance that will ensure “citizens will be on their best behaviour:
According to Guardian analysis of publicly available data, Peter Kyle met people close to or representing the sector 28 times in a six-month period. That was more than one meeting every week on average, and nearly 70% more often than his predecessor as science and technology secretary, Michelle Donelan.
Many of those meetings were also attended by Matt Clifford, the prime minister’s adviser on AI, who has been criticised for carrying out his role while also holding shares in dozens of AI companies.
Earlier this year the Guardian revealed that the government was delaying its plans to regulate the AI sector.
Last September, Kyle met Tony Blair in a meeting designed to “discuss [his department’s] priorities”. However, information obtained by Politico last week under freedom of information laws shows Blair used that meeting to suggest Kyle meet the Ellison Institute of Technology, which is funded by Larry Ellison, the billionaire tech mogul who also funds the Tony Blair Institute.
Kyle was also involved in watering down proposals from a Labour backbencher to ban addictive smartphone algorithms aimed at young teenagers.


Of course Komisar Starmer likes this totalitarian panopticon. He serves something, just not his compatriots.
In spite of serious consequences in every area that he operates, Blair just never gives up on providing us with potential for major comedy!
He is a political clown of the first magnitude, and his baleful influence is stamped all over the current iteration of New Labour, as it aimlessly ambles over the political landscape of the UK, leaving chaos and great disillusionment.
Thank you, Ludus.
I despise the Blairs as much as the next person, if not more so*, and recognise their malign influence, but don’t consider them clowns**.
*I live near the Blairs in Buckinghamshire and note how wealthy they are and how, for example, they treated lock down rules like Leona Hemsley treated taxes. The family are war mongers, but live well and well away from the front.
**I consider the likes of Jeremy Corbyn and his consigliere John MacDonnell clowns. Why? Here you are:
https://www.mirror.co.uk/news/politics/john-mcdonnell-invites-peter-mandelson-9949314 and
https://labourlist.org/2017/02/mandelson-i-am-working-every-day-to-bring-down-corbyn/.
Corbyn and many, but not all, on the left refuse to learn the lesson. He’s on the campaign trail with Zach Polanski, the same guy written about per https://www.buzzfeed.com/jimwaterson/let-our-friend-stay-corbyn-insists.
In 1993, a columnist, whose name I forget, warned in the Racing Post, sic, of “Old Etonians in Liberal Democrat clothing”. He was talking about the Newbury byelection and David Rendel. One should beware of Liberal Democrats and austerity fans who jump ship, due to not securing a seat, to the Greens.
As Alexei Sayle says about the Greens. They are Liberals on a bicycle.
For those less familiar with Alexei Sayle, here is a little track to cheer you up. I hope this is okay with the moderators. In one of the videos he even rides a bicycle but vid quality is Z Z – – -;
https://www.youtube.com/watch?v=Orn6VLsWsKI
Thank you, Nick.
A cabinet reshuffle / the third reset since the July 2024 election is rumoured for the summer. Kyle is fancied to replace Bridget Philipson as education secretary and combine that with his current role, in part to save money.
Such a move will facilitate a greater role for this young man’s business: https://bmmagazine.co.uk/news/sales-rise-at-euan-blairs-multiverse-but-annual-losses-widen-to-60m/. The youngster counts Rishi Sunak as a friend and investor.
With regard to profit, Blair closed Tony Blair Associates in 2016, but retains clients in a personal capacity, bills directly and has the fees paid to his accounts at JP Morgan.
Thanks, Colonel.
In research for this post, I stumbled across an article about Kyle’s passion for apprenticeships. Now it all makes sense. Yet another grift for the Blairs and their coterie to sink their teeth into.
Thank you, Nick.
You’re very welcome.
From the 1990s, the Blairs made money from student accommodation, an empire they retain. Now that universities are going bust, the family needs a new source of income.
Near the end of New Labour’s reign, it was reported that Blair and his team were digitally illiterate. He didn’t know how his computer worked; all emails had to be printed for him.
Perhaps this explains his thrall for digital fantasies today, and his fealty to L Ellison.
If it’s online, then it is insecure and can be hacked. And when it is hacked, government ministers will say that mistakes were made and we have learned our lessons and it will never happen again, even though all that information is already on the black market. Saw an example of this a coupla years ago here in Oz. So the Federal government was setting up what they called ‘My Health Record’ with the idea being that you can be anywhere in Oz and if you or a doctor at a hospital needs your medical information, it is all there online for convenience-
https://www.digitalhealth.gov.au/initiatives-and-programs/my-health-record
Sounds logical, right? So as it was being set up, we were sitting in a hospital when one of the staff came around with this board asking if we would like to sign up to it. We politely said no. The government was keen on getting as many people to sign up as possible to show that it was a roaring success but that was not why I refused. I read that they had not even set up the security systems on this yet but the Minster dd not want to miss some arbitrary deadline so went ahead with it anyway. Gawd!
Just a thought – if this goes through in the UK and when they ask about bank account info, see if they are asking for all of them or just one. If just one, set up an account but only keep a minimal amount in it and don’t list your main bank account. You can guess why.
Thanks. I’d long ago set up 2nd bank account where my main money is and is not used for anything else. The “usual” account was the one I set up on day one at uni, many decades ago.
Regarding health care security: long before NHS-accredited clinical trials started to move beyond only that the data be password protect with paper questionnaires in a locked filing cabinet (sheesh) I had migrated all my survey data into drives secured using Truecrypt. I use the last produced version to this day. Very suspiciously, it was announced that it was insecure and a new program called Veracrypt was to replace it.
I called BS straightaway. I saw online on forums that GCHQ “hated” Truecrypt; a mathematician I went to uni with and had worked at GCHQ has said nothing since it might get him into trouble for supposedly violating the Official Secrets Act (which he had to sign) but which led me to believe these warnings on certain (primarily Linux lovers) were in fact a warning that Veracrypt was set up with deliberate backdoors for GCHQ etc. This is obviously all alleged with the usual caveats re hearsay but I love that quote from Yes Minister/Yes PM “Never believe anything until it is officially denied”.
Thank you, Terry.
Does your friend have anything to say about https://www.mirror.co.uk/news/uk-news/spy-bag-mystery-mi6-agent-33204449?
I remember that story but sadly my ex-GCHQ friend and I have lost touch…..he became an actuary (after his two closest uni friends, me and another left the profession for being boring beyond words!) and apparently these days has a comfortable life in Bucks doing very little and living off good investments!
Hey ho, whatever floats your boat!
I still remember with a good guffaw the interview I had at Cambridge with an unidentified guy (undoubtedly Mi5) who wanted to check up on him. I was horribly hungover and just wanted him gone but he was doing “subtle” tests on *ME* – the then Prince Charles was visiting and his helicopter was visible from my college window and the interviewer excitedly wanted me to look. I didn’t want to move in case I puked so did a “whatever” so my “character evaluation” was probably ignored as “guy whose grandfather was Irish and whose views should be discounted”. Irony is my grandad survived the Battle for Caen and should have got a medal.
I did something similar myself. I opened one account with Lloyds, the other with Halifax. Maybe 25+ years ago. Anyway somewhere along the line one bought the other so now when I call one of them, they can see my account in the other. They make little cute comments about money moving in or out of each. I am now looking for an obscure building society to set up another one. Post Office maybe?
Nationwide remain a proper old-school Building society. They even pay periodic cash payments to members of good standards as a thank you (akin to a dividend from a bank) but they’ve been a magnet for people who believe in the old system like the Post Office Girobank (RIP).
I said once on here or as a YT comment that we really really should be resurrecting Girobank, and the Post Office as part of NHS reform. So EVERY adult has an automatic account which can be used to charge you (say) GBP10 for a GP consultantion but which get you a simultaneous credit of 10 quid provided you turn up or give a good reason for being a did not attend (like being old and your carer never turned up, you had a problem with ongoing meds etc etc). Australia perfected this system almost 50 years ago. There is no excuse for not doing here in UK.
Australia even updated the system to “bulk billing” to reduce admin associated iwth doing both a credit and a debit. Apologies for increasing typos – another “long COVID I suspect” thing is neurological……ny old RSI is back. Little and ring ringer in left hand exhibiting neurological weakness. O2 levels normal so not part of my longstanding heart isues (I think).
Post Office is Bank of Ireland
As an addendum to my original comment, the NHS is getting worse not better in the age of digital stuff. If you’re an NHS employee at various levels you MUST change your password every 6 months and you can’t use an old one.
Result? 99% of consultations I’ve had with NHS clinicians I’ve spotted a post-it note stuck to their monitor with their latest password. *Smacks head* It has long been asserted that this approach to security is one of the worst for exactly the reason I just gave. Plus clinicians will sometimes leave the room when someone “trustworthy” like me is sitting there. They are very very lucky that I AM trustworthy and don’t take the 30 seconds to log in, access key medical programs (with which I am familiar, having stepped up to fill gaps via shifts in admn services during wosrt of the pandemic) and make changes.
Personally I don’t WANT to read the “other, private, notes” the docs write about me in the “second patient record!” that they all swear doesn’t exist but I know DOES. It wouldn’t be nice reading!
ERROR!
“Not to blow out own trumpet, but that is exactly what has happened.”
out > our?
Fixed! Thanks, Patrick.
Exactly!
This is all about creating control and stealing as much value as possible.
Correction?
Presumably “the UK government has a torrid track record” should read horrid.
Fixed. Thanks, Tinky.
Calling this a honeypot is wrong. This is putting all your eggs in one basket.
Being very simplistic, a honeypot is a system designed to attract attackers so that they can be observed covertly and dealt with appropriately. It’s effectively digital entrapment.
Am I being overly pedantic? Maybe, but meaning creep like this leads to confusion and misunderstandings down the line.
You’re right, Jokerstein, I stand corrected.
And you’re not being overly pedantic at all — these nuanced meanings are crucial, especially when the words in question feature in the heading — and I thank you for it. Interestingly, I’m not the only one to have (pun intended) fallen into this trap. Just a couple of weeks ago, Jasleen Chaggar, the legal and policy officer at Big Brother Watch, a prominent civil liberties and privacy campaigning organisation in the UK, published an op-ed in City AM titled “Labour’s Digital ID by the Backdoor Will be a Honey Pot for Hackers.”
Once again, the collective knowledge of the Commentariat shines through! Have changed the title to “Is UK Creating a Giant Bonanza for Hackers and…”
As many articles on this site describe the current and future contraction of energy provision, I am more concerned that by replacing existing paper based systems and knowledge of running those systems, with pie-in-the-sky-single-electronic-identity-dreams, it will make everything so much worse when the computers can no longer run 24/7.