This is Naked Capitalism fundraising week. 312 donors have already invested in our efforts to combat corruption and predatory conduct, particularly in the financial realm. Please join us and participate via our donation page, which shows how to give via check, credit card, debit card, or PayPal. Read about why we’re doing this fundraiser, what we’ve accomplished in the last year and our current goal, more meetups and travel.
Lambert here: I’m no expert in any of this, and I’m sure readers will chime in; you all know my priors on smart phones! I have no doubt that many of these measures are useful, in the sense that home burglary protection devices are useful: Against low grade operators and amateurs, of whom there are rather a lot. However, no professional would be deterred or defeated. Therefore, for any serious communication, I’m dubious about smart phones, given the overlap between cellphone manufacturers and networks on the one hand, and the national security state, on the other. This applies to Tor as well; Tor was, after all, sponsored by the government. I’m reminded by the famous Lieutenant General Van Riper in Millennium Challenge 2002 war game, who sent his opponent’s entire fleet to the bottom of the Red Sea by, among other things, going dark on his communications; he used motorcycle couriers. Of course, things may be different in Europe, and this handbook is directed to Europeans.
By Xnet (ex-EXGAE), a group of activists who have worked since 2008 in different fields relating to online democracy, the fight against corruption and the creation of mechanisms for organized citizen participation and to constrain seats of power and institutions. We defend a free and neutral Internet; the free circulation of culture, knowledge and information; citizen journalism and the right to know, to report and to be informed; the legal, technical and communications struggle against corruption and technopolitics, understood as the practice of networking and taking action for empowerment, for justice and for social transformation.
The Spanish Government’s crackdown in Catalonia has shown that the entire population – not only Catalan people – needs tools to guarantee their fundamental rights. Here’s a practical guide to securing them online.
What is happening in Spain these days in relation to the situation in Catalonia is a very significant milestone in the defence of freedoms and rights around the world in the digital age.
The reaction of the Spanish government has clearly shown that the entire population – not only those living in Catalonia – needs to have tools to guarantee their fundamental rights (natural rights guaranteed per se which do not depend on any government) independently of any unjustified or arbitrary tutelage.
Many international institutions like the United Nations, recommend this after the Snowden revelations, emphasizing that knowledge and use of digital tools by everyone to ensure their privacy, freedom of expression and access to information are essential and the only way to guarantee fundamental rights in the face of increasing state-approved mass surveillance.
The acceleration of events in Catalonia has finally made the whole Spanish population aware of this situation and many citizens are now ready to begin use these tools. These days, in contrast to situations such as those experienced in Turkey, for example, even the Catalan institutions are publicising the necessary tools. They have finally agreed to assign, distribute and share responsibility for protection of freedoms, thus beginning to endorse what we see as the embryo of what has to be a democracy that is up to the requirements of the digital age.
Xnet fights to empower people because we believe that a real democracy resides in the fact of making it possible for each and every person to access the necessary tools to monitor their institutions and to be autonomous in their judgments and, consequently, in protecting their rights and freedoms. We have worked tirelessly to teach people how to use these tools and to deactivate the gross attempts to criminalise them by powers that require people to be at their mercy.
From this point of view, what is happening these days is of historic significance and hopeful. This acceleration towards a greater degree of democracy and strength for civil society is taking place spontaneously. But lack of information about some aspects of the digital milieu is exposing people to risks.
Accordingly, and in order to facilitate this process of co-responsibility wherever necessary, Xnet has summarized the most important information in a basic How-to guide.
Our How-to guide is also associated with the indispensable work in defence of rights and legal freedoms carried out by several organisations in the campaign #SomDefensores.
Basic How-To Guide for Preserving Fundamental Rights on the Internet
Xnet has prepared this technical guide with tips and tools addressed to activists, journalists and citizens whose fundamental freedoms and rights on the Internet are being restricted by state powers or authoritarian governments.
It is important to read the recommendations, download and learn to use these tools before a possible arbitrary blocking of the Internet, or the concerted attempt to access the private data of citizens, etc. Because, once it starts, it will be too late.
This guide is to be improved collectively; if you have any corrections write to: info[at]xnet-x.net /Clave pública PGP.
Arbitrary Website and Application Blocking
Arbitrary Internet blockages occur primarily – but not only – when a government intentionally disrupts access to websites, mobile applications or electronic communication services to censor or control what people say or do.
Internet access is essential for the exercise of our freedoms and should be considered in itself a fundamental right [#KeepItOn]. Partially or totally blocking Internet access is a common practice in countries with authoritarian regimes, for example, to avoid access to certain types of content (in opposition to the regime, LGTBI, etc.) and to exercise control over conversations and the flow of information.
How to Access Websites that Are Arbitrarily Censored or Blocked in a Particular Connection/Location: Tor and VPN
Both the Tor network and a VPN allow access to websites and applications that have been improperly blocked in a region or country, surfing the Internet as if it was being done from another geographical location.
For example, if a country blocks access to Twitter, people can use the Tor network or a VPN to access the social network as if their connection was coming from another point or country where these arbitrary restrictions on freedom of expression and access to information are not happening.
Moreover, navigation in both cases is encrypted – in a “closed envelope”, so that it can only be read by the sender and receiver.
Tor for Android: Orbot
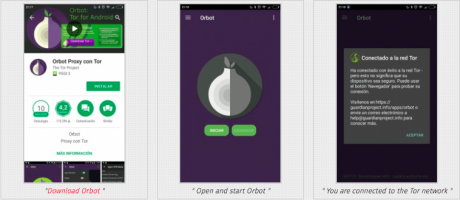
- Download Orbot
- Open and start Orbot
- You are connected to the Tor network
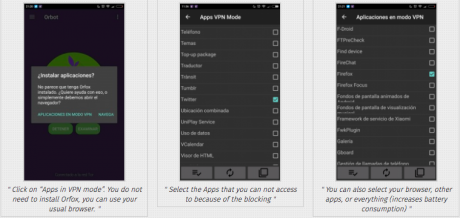
- Click on “Apps in VPN mode”. You do not need to install Orfox, you can use your usual browser.
- Select the Apps that you cannot access because of the blocking
- You can also select your browser, other apps, or everything (increases battery consumption)
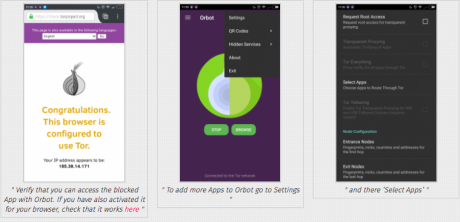
- Verify that you can access the blocked App with Orbot. If you have also activated it for your browser, check it works here
- To add more Apps to Orbot go to Settings
- and there ‘Select Apps’.
Tor for iPhone: Onion Browser
There is no iPhone application that allows use of the Tor network for any application installed on the device. However, with Onion Browser you can access websites and the web version of arbitrarily blocked applications.
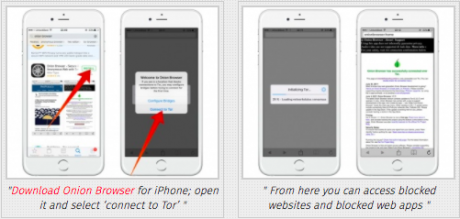
- Download Onion Browser for iPhone; open it and select ‘connect to Tor’
- From here you can access blocked websites and blocked web apps
Tor for PC: Tor Browser
Download Tor browser for Linux / MacOS / Windows.
How to install and use Tor in Linux / MacOS / Windows.
Video: How to use Tor in PCs created for the launching of the Whistleblowing Platform against corruption of the City Hall of Barcelona (CAT):
VPN
A VPN (Virtual Private Network) allows your data to travel through an encrypted connection, or a kind of tunnel, before heading out to the open Internet, to connect to the Web from another location.
The easiest and fastest application to install in order to activate a VPN connection is Bitmask, which is also free. At the moment it is only available for Android phones and Linux PCs, although its version for the MacOs iPhone is about to be released and, in the not too distant future, its Windows version. However, there are many very low-cost payment services that offer VPN connection for all types of devices – see below for information on Internet services that ensure the preservation of privacy and information.
It is advisable to have both Tor and VPN options. If traffic is blocked through Tor, you can then use the VPN, and vice versa.
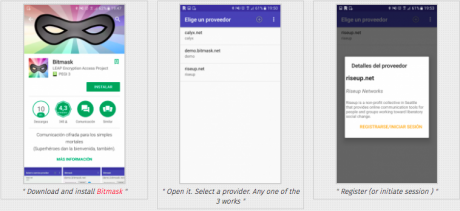
- Download and install Bitmask
- Open it. Select a provider. Any one of the 3 works
- Register (or initiate session)
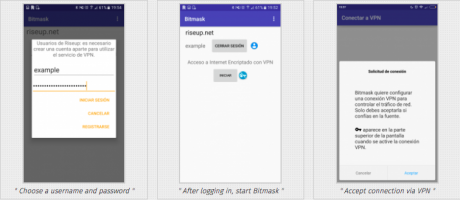
- Choose a username and password
- After logging in, start Bitmask
- Accept connection via VPN
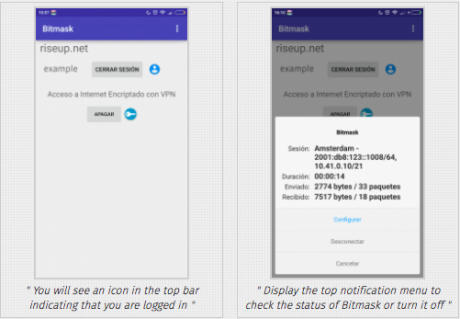
- You will see an icon in the top bar indicating that you are logged in
- Display the top notification menu to check the status of Bitmask or turn it off
For a correct configuration of the VPN connection, it is important to ensure that you are not suffering ‘DNS leakage’. Otherwise you will not be able to overcome the blockade and will reveal your connection data. In the page DNS Leak test you can find out how to test it and how to solve it.
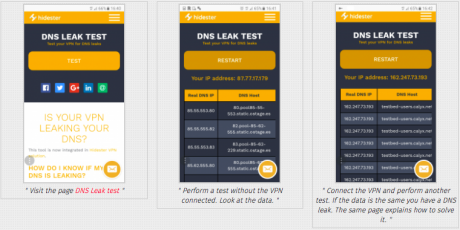
- Visit the page DNS Leak test
- Perform a test without the VPN connected. Look at the data.
- Connect the VPN and perform another test. If the data is the same you have a DNS leak. The same page explains how to solve it.
#Mobile Device Encryption
Encrypting devices, especially mobile phones, is essential to maintain the privacy of personal data should they be lost or stolen. This is why most smartphones have installed by default tools which, in a few simple steps, encrypt the entire device, and it always is recommended to protect the privacy of data, accounts, contacts and user information.
Mobile Device Encryption: Example with Android
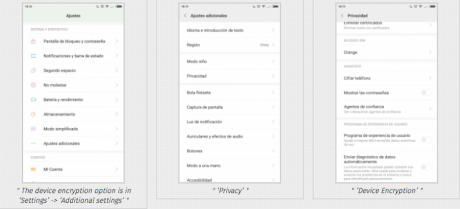
- ‘Additional settings'”>
- The device encryption option is in ‘Settings’ -> ‘Additional settings’
- ‘Privacy’
- ‘Device Encryption’
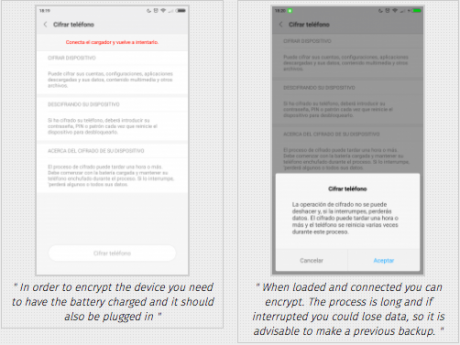
- In order to encrypt the device you need to have the battery charged and it should also be plugged in
- When loaded and connected you can encrypt. The process is long and if interrupted you could lose data, so it is advisable to make a previous backup.
In general, as a good practice, you should not store unnecessary information in your devices, delete periodically. Even though you may be sure that everything you have is absolutely legal, remember that it is not you but the power who decides what is legal and what isn’t, and what today is legal might not be so tomorrow in the event that the regime becomes authoritarian. Deleting and emptying the bin is not enough, you have to use specific tools that overwrite the data several times. More information and tools to do it here (a backdoor was discovered in CCleaner for Windows that has already been patched: always download the latest version).
Note to the Spanish State: In the case that security forces confiscate someone’s device because this person is under investigation, he or she has the right not to reveal encryption keys, PIN, unlock pattern, password or similar data, in accordance with the right not to testify against oneself (Criminal Procedure Law Art. 118 h & Art. 588 septies b 2; as explained in this document to the Secretariat of State of the European Union).
# Hosting: Privacy and Security
The censorship of websites by authoritarian governments can happen at a deeper level when, instead of blocking access to the web through the network, the page is entirely closed down either by intervening in the servers or by seizing the domain. In this case, tools like Tor or a VPN will not help.
In order to foil such attempts (or create a mirror-copy of the same website – in a secure hosting if the web has already been censored), citizens living in authoritarian states should not choose a server within the territory of their country. It is necessary to search and choose countries where the legal framework offers strong guarantees regarding freedom of expression and information about where to locate the hosting.
Neither should they register the domain of a website susceptible to be censored with Top Level Domains of their own country. It is easier for a government to intervene in its TLD than in others such as .net, .eu or .is. In Spain, we have recently experienced a preposterous example of this, unprecedented in the European Union, with the TLD .cat:
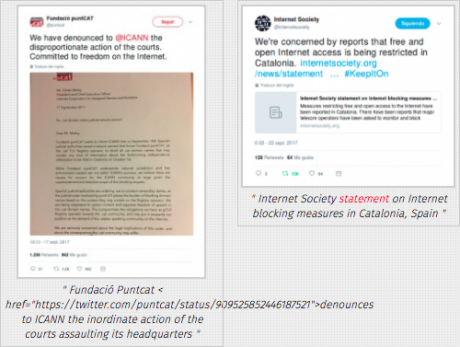
- Fundació Puntcat denounces to ICANN the inordinate action of the courts assaulting its headquarters
- Internet Society statement on internet blocking measures in Catalonia, Spain
Finally, to protect your privacy and security (to avoid spam, spam, or other harassment), you should acquire your domain in registration services that offer strong legal security, eg Njalla.
Many domain registrars undertake not to publish the owner’s data and to manage the requests they receive themselves, whether they are requests from buyers, individuals, or authorities and institutions. This type of service is known as private whois.
The importance of this requirement can be understood by entering, for example, https://whois.icann.org/ or https://www.nic.es/sgnd/dominio/publicInformacionDominios.action (for domains ending in .es) and looking for any web.
A file will appear in which all data will be output. If the person who owns the website has not used a provider which had undertaken to protect their privacy, his or her information will be published, and anyone from anywhere can see it:
- REGISTRANT CONTACT (note that providing inaccurate or outdated information is punishable )
- Name: …
- Organisation: …
- Street: …
- City: …
- State: …
- Postal Code: …
- Phone: …
- Email: …
If the owner has taken the functional and customary measure that the requests are to be managed by the provider (has activated the private whois service), the data will be forwarded to the service provider. The provider will notify the owner if someone has searched or required it. It is important that the provider should assure you in the contract of the deadlines within which it provides you with the information. The more ethical providers who are respectful of the rights of their users usually offer deadlines between the requirement and the communication of your data to those who require it if you have not answered.
Not all domains agree because not all domains are managed in the same way. Generic domains, .com, .net, .biz, .org, etc… are managed by ICANN – the Internet Corporation for Assigned Names and Numbers, the leading Internet governance body, and this organization is the one which permits the use of domains that can have recourse to Whois protection. The .es domains, on the other hand, are managed by Red.es and these domains do not allow hiding the data of the registry of users who want to acquire an .es domain.
# Messaging, VOIP, Email and File Sharing Privately and Securely
Massive surveillance of what we do and say on the Internet (and in all electronic communications) by governments has been clearly revealed thanks to Snowden’s revelations. Below are some tips to help defend privacy against these practices using encryption tools.
Messaging
To protect the privacy of your communications always use messaging applications that have end-to-end encryption by default. We strongly recommend using Signal (Android | iPhone), an end-to-end encrypted messaging app whose use is easy and intuitive, and recommended by Snowden himself. Among other popular messaging applications, Whatsapp has also integrated end-to-end encryption in all communications by default (however, Facebook has already shared user data with WhatsApp and the social network, so Signal is still the best choice). Telegram, has an encryption option but is not active by default.
It is important to note that, even though they are encrypted end-to-end, the above applications are associated with the user’s mobile number. Hence, even if the communication is encrypted (a third person cannot see the content) it is not anonymous and the identity of the sender and receiver, as well as connection and geolocation times are known.
Video calls – VOIP
You can make encrypted calls and video calls over the Internet with Signal (and Whatsapp) to a contact. MeetJitsi allows you to make group video calls. Calls and video calls through Skype, Hangouts or others do not sufficiently protect the privacy of your communications.
Encrypted Email
In the case of e-mail, it is important to know that all e-mail sent and received can be read (and is actually processed) by the mail service providers. Some of them, when required by the authorities, show little concern about the privacy and legal security of their customers/users. We do not recommend the use of services like gmail, yahoo, hotmail, etc. In any case, it should be known that sending any email without encryption is almost the same as sending a letter in an open envelope. In order to protect the right to confidentiality of communication, it is possible to use encryption with PGP. This allows you to ensure the privacy of communications and files sent via email. This guide from Security in a Box explains how to use email with PGP with Linux | MacOS | Windows.
Again in this case, the communication is encrypted in terms of content, but not anonymous.
What does this mean? It means that, even if we do not indicate our name, or we use an email account in which our identity does not appear, or a throw-away one, all electronic communication leaves a trail , the so-called IP address, which is a unique address assigned to each device on the network and indicating the point from which a communication has been made. In addition, the sender, recipient, and subject of the message as well as other “metadata” of the mail are not encrypted and indicate who receives it, when, and other data. Therefore, the real anonymity possible for transferring files and information can only be achieved through the Tor network, because this communication is not made from point A to point B but the connection passes through several intermediate nodes within the Tor network, none of which knows the origin and destination at the same time. Obviously, accessing our regular account of gmail or any social network through the Tor network will reveal the identity even if the IP address is hidden.
One example of how to deliver information privately and securely is the XnetLeaks mailbox for reporting corruption, based on Globaleaks and accessible through Tor.
#Blocking of Messaging Applications
Alternatives to private and public communication in case Signal or Whatsapp messaging applications and social networks are blocked.
FireChat: for Android and iPhone
FireChat is a messaging application that allows communication between devices and publishing in public forums between nearby devices through mesh-networks.
-
Public rooms: like #PublicRoom1, are open chats in which all messages reach all participants in the chat. All messages are public and not encrypted. The creators of FireChat recommend that people should not use personal data and that they should be careful with personal information that is shared in the public chats.
-
Private Messages: Private messages are encrypted and can only be viewed by the sender and the recipients, which can be one or several.
This is the application used by demonstrators in the yellow umbrella revolution in Hong Kong when their communications were blocked. Julian Assange recommends it (along with Briar) for this type of situation.
Download FireChat for Android or iPhone: https://www.opengarden.com/firechat.html
How to use FireChat: https://www.opengarden.com/how-to.html
#Internet Shutdown
In the extreme case of a shutdown in which the Internet connection is completely cut off, as happens in situations of great repression, there are applications that allow communication between mobile devices, even without connection.
Briar: for Android
Briar is an open source messaging application designed for activists, journalists and anyone else who needs a secure, easy and robust way to communicate. Unlike traditional messaging tools such as email, Twitter or Telegram, Briar is not based on a central server: messages are synchronized directly via p2p between users’ devices.
If the Internet is down, Briar can synchronize messages via Bluetooth or Wi-Fi, and thus maintain the flow of information in case of crisis. The devices must be able to connect between them so the maximum distance in the case of Bluetooth is 70 meters approx. or a little more in the case of Wi-Fi depending on its scope. In the case of groups or forums, the larger the group the greater the reach of p2p synchronization.
With Internet connection, Briar is synchronized through the Tor network, protecting users from surveillance.
Download Briar: https://briarproject.org/download.html
Howt to use Briar: https://briarproject.org/manual/
#More
This guide contains a series of basic guidelines for preserving your rights on the Internet. For greater security and privacy on the Internet, visit Security in a Box: https://securityinabox.org/.
The manual “Zen and the art of making tech work for you” to read more about creating and managing online identities as well as about building and maintaining secure spaces online and in physical life: https://ttc.io/zen
MyShadow to read and learn about tools and methodologies to understand and change your digital shade: https://myshadow. org/en
Finally in terms of basic logistics, it is recommended that you should always leave home with your devices charged and, if possible, with external batteries for greater autonomy.


Thanks. Think I need to spend a lot of time digesting this. Definitely had/has implications for me.
Yves went to great trouble (thanks!) to explain why things at “my end” might be causing my commenting problems but I need to do a lot more it seems.
Though for the record, I’m less bothered about concealing my “real identity” (it being so easily determined, particularly if like me you’re a former senior academic) but more bothered about general security/email issues for me and my company.
There is also Tails (https://tails.boum.org/) as an option. You boot the computer from a DVD or USB stick into a Linux operating system. You can use this while you are working though any files you want to save would have to go onto a USB stick or external hard drive. When you are finished, you reboot your computer into its regular operating system. A quote from their site-
“It aims at preserving your privacy and anonymity, and helps you to:
-use the Internet anonymously and circumvent censorship;
-all connections to the Internet are forced to go through the Tor network;
-leave no trace on the computer you are using unless you ask it explicitly;
-use state-of-the-art cryptographic tools to encrypt your files, emails and instant messaging.”
I’m not sure whether NC draws the sort of activist population this is addressed to, but if the topic comes up with someone to whom it is pertinent, here’s a thought:
Technolgy leverages the ability of a small group to do more against a less organized and empowed larger group. This is all well and good, but it’s more likely to give you a false sense of security, essentially if you pose a real threat to anyone other than your spouse, employer, or small town police department.
If you get into the deep end of the activism pool, your advantage is in numbers of people. With the increasing disparities between the People and those seeking to control them with technology, THIS is your strength.
Couriers may be slow and paper cumbersome, but they are far more difficult and less cost efficient for a very small minority to defend against. Read some old spy novels for the various tricks. It’s hardly a matter of being a ludnite.
Use the technolgy, but know that you can and will destroyed if you ever pop up on their radar, which is better than your countermeasures ever will be. Using an encrypted phone or PGP only draws attention. Ditto with any tool that digitizes.
Take compartmentalization seriously. Keepr leadership and strategic planning functions seperated from operations. Use tech to manage your flash-mob, but then start the tech framework for your next op from scratch.
You get the idea.
This may be a little bit of a tangent, but it is related to this article. One thing U.S. residents can do right now is to contact their Senators and ask that they vote against the renomination of Ajit Pai to the Federal Communications Commission. He is a devoted enemy of net neutrality, and we need to get him out of the government. The vote will happen soon, since cloture has been invoked.
https://www.congress.gov/nomination/115th-congress/89
Senate contact info:
https://www.senate.gov/senators/contact/
My first reaction was that this is something to think about in the coming years. But then I played out a new Korean War scenario in my mind. Since it would be a horrible fiasco from the get go, I could see digital repression being an integral element of war plans.
Following links from the encryption story, I came upon a short video, in Spanish, promoting a play called “Become a Banker; black cards …”. Doing a search for the play, I found no results on Google, ‘cept for the *paid, go-to-school-here* kind.
The short trailer looks humorous and irreverent. A really big scandal? NC readers more info?
Link is here:
https://xnet-x.net/en/become-a-banker/
Here the full theatre show ;)
https://www.youtube.com/watch?v=PGZqKRjhf3o
I tend to agree with Lambert that smart phones are likely less secure even with measures described here (though I’m certainly no expert), and the linux platform probably most secure if measures taken, see The Rev Kev above. Surveillance in the US of US citizens goes way back – before it was a few, now everyone is recorded and the security state agencies sift the data at their leisure. Worth noting that, depending on your politics, you may not be concerned about Trump and his administration finding out all your writings, future rulers might not be so benign.
These are some of the same technologies that have made anonymous speech on the internet so hard to stop – which is great, until you realize it enables anonymous harassment, death threats, fraud and fake news – all issues Ted Nelson pointed out in his critique of hypertext back in the *1960s*. You need to know the identity of the speaker so you can build a reputation about the quality of their information. (There is, by the way, infrastructure that would allow pseudoanonymity and square this circle with reputational responsibility, but the Valley has always been unusually hostile to it.)
Do you want guys running around on public roads in cars with tinted windows and no license plates? Care to revise your opinion in light of the fact we have people stockpiling assault rifles and carrying out mass shootings? Now take away the AK-47s and substitute CRISPR-engineered viruses. Still comfortable with perfect anonymity?
You might not like suppression of dissidents by the Iranian or Chinese nation-states, but the state still has important functions to perform. And handing North Korean hackers anonymous access to the internet from which they can hack our accounts doesn’t seem to be the risk-free proposition this article makes it out.
There will always be grounds for warranted searches. Don’t let the way other people break the law undermine your support for it.